How to clean your website from Virus eating your WordPress or Website Bandwidth
If your website is consuming an abnormal amount of bandwidth, don’t be too quick to celebrate – it might not be because thousands of people love your content. In fact, it could be due to a hidden malware script consuming your server resources to the point of crashing your website.
This is a personal story – a painful and technical journey that lasted almost five days. But if you’re facing similar issues, I hope this article saves you time, money, and frustration.
What Is Bandwidth in simple Terms?
Imagine your website as a tap and water as the data it serves – pictures, text, videos, etc. Now, bandwidth is the size of the pipe that allows this water to flow. The more users that access your site and the larger your content (images, videos, pages), the more “water” (data) flows through that pipe.
If the pipe is too small or too much water is forced through it, it gets overwhelmed, leading to slow loading times or even site crashes.
Now imagine someone secretly connects a huge hose to your tap and starts draining gallons of water every second. That’s exactly what malware does when it consumes bandwidth – it overwhelms your website’s server resources, crashes it, and sometimes gets your hosting account suspended.
My Nightmare Began…
We had a website hosted on a fairly good server. Everything was working fine until suddenly, our site started going offline every 24 hours. I would reset the cPanel login, WordPress login, change FTP passwords, and everything would be okay for a while – then BOOM – the site would be down again the next day.
At first, I thought it was a plugin conflict, so I deleted the plugins folder.
Still no change.
Then I thought maybe it was the theme, so I completely deleted the WordPress theme and uploaded a fresh one. But that didn’t help either. Every time, the server usage would shoot up – 20GB of bandwidth per day was being consumed by something I couldn’t see.
Even servers with “unlimited bandwidth” plans have their limits. When something chews through that much data daily, your website slows down drastically or is shut down for overuse.
This went on for 4 days.
The Breakthrough – A Hidden File
On day 5, I went deeper into my cPanel file manager and decided to check even the hidden folders. That’s when I noticed the “.well-known” folder. For many of you, this is a legit folder used by SSL providers for Let’s Encrypt certificate validation. So, most people ignore it or never bother to open it.
But something felt off. So I opened it.
Inside, I found a suspicious file called:
My instinct screamed at me that this shouldn’t be here. So I opened the file and BOOM – there it was – a script that looked like this:

I won’t post the full version here for safety reasons, but it was looping a massive number of HTTP requests to the server itself and other unknown IPs, basically creating a DDoS-style attack from within my own website!
This tiny file was eating up 20GB of data every day.
Why This Was So Dangerous
Here’s what made this especially dangerous:
-
It was hidden in a normally trusted folder (.well-known).
-
It didn’t trigger standard plugin-based malware scanners.
-
The script ran silently – unless you monitor server logs or bandwidth usage manually, you’d never know.
-
It reset itself – sometimes these scripts even have cron jobs or self-replicating commands elsewhere on the server.
-
The WordPress login, plugins, or themes were not the issue – which made troubleshooting incredibly frustrating.
Lessons Learned (And What You Should Do)
-
Always inspect hidden folders in your cPanel
Click on “Settings” in File Manager and enable “Show Hidden Files (dotfiles)” – especially if you’re facing strange bandwidth spikes. -
Check the .well-known folder regularly
This folder is often overlooked but has become a common target for hackers since it’s normally whitelisted by SSL and ignored by site owners. -
Don’t just focus on WordPress plugins and themes
Sometimes the threat isn’t where you expect it to be. Even if you reset WordPress or install a fresh theme, the real malware might be hiding in a system folder. -
Install a file change monitor
Use plugins or server tools that monitor file changes and alert you when a new PHP file is added to any directory – especially system or hidden ones. -
Use server-level malware scanning tools
If you have WHM or root access, use ClamAV, Imunify360, or even third-party tools like Malware Expert to do a deep scan of all server directories. -
Check your server logs
Look at raw access logs and bandwidth logs under cPanel’s Metrics section. You can see exactly which files are being accessed the most. -
If all fails, consider hiring a security expert
I lost four days of productivity and sleep because of this. Don’t let ego or budget keep you from hiring someone if you’re stuck.
A detailed look at this File

The PHP code you’ve shared is malicious. It’s a typical example of obfuscated malware, which is used by hackers to:
🚨 What This File Does:
-
Obfuscates Payloads:
The functiongmuk($jxt)is trying to hide actual malicious code usingchr()and custom string functions. This makes it harder to detect by human eyes or antivirus scanners. -
Decodes and Executes Malicious Code:
The line: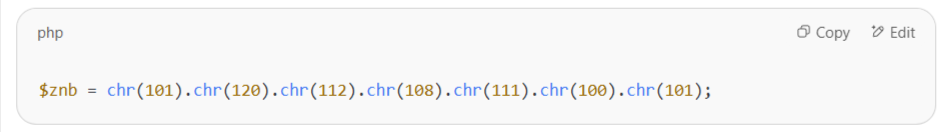
-
spells out
explode, which is then used to break up a large, encoded string and likely latereval()orbase64_decode()it to run malicious PHP. -
Hidden Webshell / Backdoor:
It contains HTML content inside encoded text—possibly used to render fake login pages or admin panels, or collect passwords. -
Command Execution & File Manipulation:
Hidden inside the encoded text, there are keywords like:-
file_put_contents -
return confirm() -
method="post" -
input type="password" -
upload -
edit -
delete
These suggest file upload, file deletion, and arbitrary command execution.
-
-
Phishing or Control Panel:
The presence of<form method="post">,<input type="password">, and phrases like “You do not have permission to access / on this server” is a sign that this might be a web shell disguised as a 403 error page or a fake admin login.
⚠️ What You Should Do Immediately:
-
DELETE This File ASAP.
-
Check for Similar Files:
-
Look for any files with random names like
abc123.php,temp.php,shell.php, etc. -
Use a file scanner or run a search for keywords like
base64_decode,eval,system,exec, orgzuncompress.
-
-
Scan Your Website:
-
Use tools like:
-
Wordfence (for WordPress)
-
VirusTotal (for individual file analysis)
-
-
Check User Uploads & Permissions:
-
If your website allows file uploads, ensure there are file type restrictions.
-
Prevent
.phpuploads via.htaccess.
-
-
Change Passwords:
-
Especially for cPanel, FTP, hosting dashboard, CMS admin, and database.
-
-
Restore From a Clean Backup, if available.
🧠 Summary:
This file is malicious, obfuscated, and most likely part of a web shell or backdoor attack. It is not safe to keep or even clean manually without experience. If you’re unsure, seek help from a cybersecurity professional.
